Guides & Tutorials
API Authentication: Methods and Best Practices
Why is API authentication required?
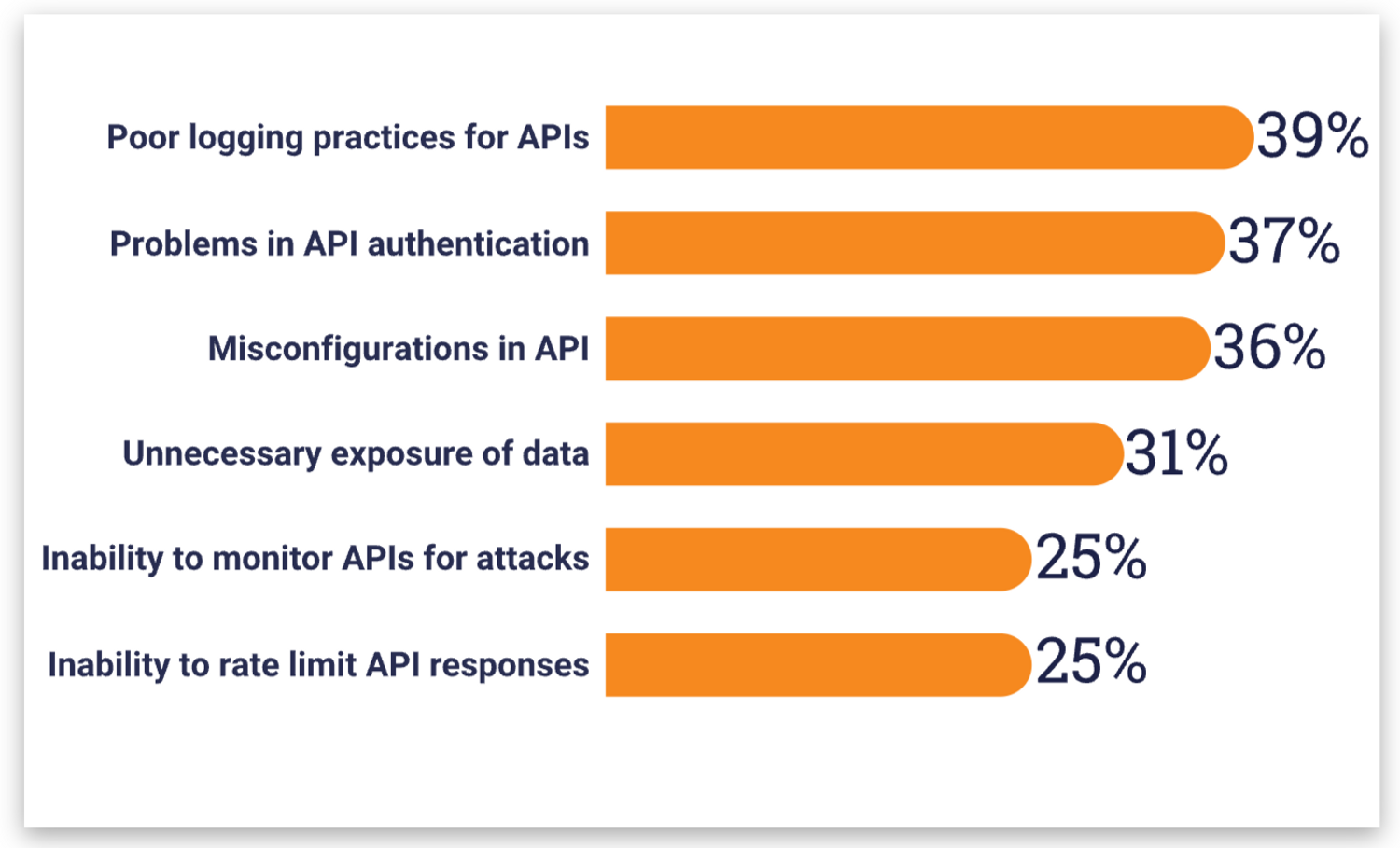
APIs continue to play an important role in modern web development, driving innovation for mobile, SaaS, and web apps across a wide array of sectors like finance, retail, healthcare, and more. However, because APIs expose application logic and sensitive data such as Personally Identifiable Information (PII), they represent a significant area of vulnerability for organizations worldwide. In fact, according to the 2022 API Security Trends Report by 451 Research, 41% of surveyed organizations had experienced an API security incident in the last 12 months, and poor practices, authentication issues, and misconfigurations were some of the top cited challenges.
Authentication vs. Authorization
To better understand methods and best practices around API security, it is important to distinguish the difference between authentication and authorization.
Authentication is the process of verifying the identity of the user (making a request to an API), and authorization is the process of verifying the properties, data, or other types of information the verified user can access. For instance, if you went to a concert and had to show your ID to be admitted into the venue, that process would be authentication. Similar to how there are different forms of IDs such as a passport, driver’s license, and credit cards, there are various authentication types that could be password-based, token-based, multi-factor, and others.
Authorization, on the other hand, would occur when security or concert staff tries to confirm the seating assigned to your ticket. If you had purchased nose-bleed seats but tried to access the VIP lounge or a meet-and-greet backstage session, you would be denied access because you do not possess the necessary authorization credentials.
What are the most common types of API authentication?
Transport Layer Security (TLS)
TLS is an encryption protocol that authenticates the server in a client-server connection and safeguards communications between client and server to prevent third parties from extracting sensitive information. Since the vast majority of today’s websites are already enabled with TLS (in fact, all traffic over Netlify’s networks is TLS encrypted), which can be identified with URLs that begin with https:// instead of http://, every web API should also use TLS to complement other authentication measures already implemented.
TLS and its one-way authentication provides sufficient protection for most sites and web apps by ensuring that private data and API credentials are kept secure, encrypted, and unaltered as they traverse across the Internet. However, for select organizations that leverage zero trust security models, mutual TLS (mTLS) would be more appropriate. In fact, Skype relies on mTLS to protect its business servers against access breaches and most B2B API communications use mTLS. The important distinction for mTLS is that it uses mutual authentication for both the server and the client, which provides additional protection against credential stuffing, malicious API requests, spoofing, and phishing.
An added bonus for TLS is that because it is a cryptographic protocol at the network layer, there is no implementation work required at the code level in applications. To establish TLS connections, applications can simply rely on existing libraries.
OAuth 2.0
OAuth 2.0 is a widely used standard for API authentication, since it provides a secure and convenient way for users to grant third-party applications access to their resources without sharing their passwords.
One of the main advantages of using OAuth 2.0 for API authentication is that it allows users to selectively share their data with third-party applications. Instead of sharing their username and password with the application, users can grant access to their data by authenticating directly with the API provider and authorizing the application to access their data on their behalf. This allows users to maintain control over their data and ensures that their personal information is not shared without their knowledge or consent.
Another advantage of using OAuth 2.0 for API authentication is that it provides a flexible and scalable solution for managing access to API resources. The OAuth 2.0 specification defines several different grant types, which allow apps to obtain access to API resources in different scenarios. For example, the "authorization code" grant type is commonly used in web apps, while the "implicit" grant type is commonly used in mobile and desktop apps. This flexibility allows OAuth 2.0 to be used in a wide range of situations, and makes it easy to add support for new grant types as the need arises.
JSON Web Token (JWT)
JSON web tokens (JWTs) are often used to implement key-based client authentication. They provide a secure and convenient way for applications to authenticate with APIs and to securely transmit information between parties.
A key characteristic of JWTs is that they are self-contained, meaning a JWT contains all the information necessary to authenticate a request, including the identity of the authenticated user and the permissions granted to that user. This eliminates the need for the app to make additional calls to the API provider to retrieve user information or to check the user's permissions. As a result, using JWTs can improve the performance of an app and reduce the load on the API provider.
Another benefit of using JWTs for API authentication is that they are signed. This means that the API provider can cryptographically verify that a JWT has not been altered. This provides an additional layer of security and ensures that the information contained in the JWT can be trusted. Additionally, JWTs can be encrypted, which means that the contents of the JWT can be kept confidential.
Rate Limiting
Rate limiting is a technique that is commonly used to protect APIs from excessive or malicious traffic. Since restrictions are placed on the number of requests that an API can accept from a single client within a specified time period, potential abuse of the API, such as distributed denial of service (DDoS) attacks or unauthorized access to sensitive data can be prevented. As a result, the API can continue serving legitimate requests, even during periods of high traffic or when it is being targeted by malicious actors.
Netlify actively mitigates DDoS attacks by monitoring for traffic pattern anomalies and spikes, and effectively controls them as needed. To learn more, check out the Essential Security and Identity eBook!
Additionally, rate limiting can be used to manage the cost of using an API. By limiting the number of requests that an API will accept, rate limiting can be used to control the amount of resources that are consumed by the API. This can be useful for APIs that are provided on a pay-per-use basis, or for APIs that are used in situations where resource usage needs to be carefully controlled.
Use the API Authentication Method Best for Your Needs
Whether you choose to use OAuth, JSON web tokens, multi-factor authentication (MFA), or other secure methods, API authentication is an essential component of API security and is crucial for protecting the information and resources that are provided by an API. Learn how Netlify uses API authentication in our Netlify API docs.


